Expose Which Attacks Can Breach Your Defenses
Use the Picus Security Validation Platform to pinpoint exploitable vulnerabilities, slash your remediation backlog by 86% and close critical gaps fast.

Attack Surfaces Expanding Faster Than Teams Can Manage
Ignoring attack feasibility in your environment bloats your exposure list with theoretical threats, leading to:
-
Wasted resources
-
Inefficient remediation
-
Security/IT team burnout
Backlog by 86%
Derived from analysis of 100M+ anonymized exposure records collected January–May 2025.
Discover the Platform
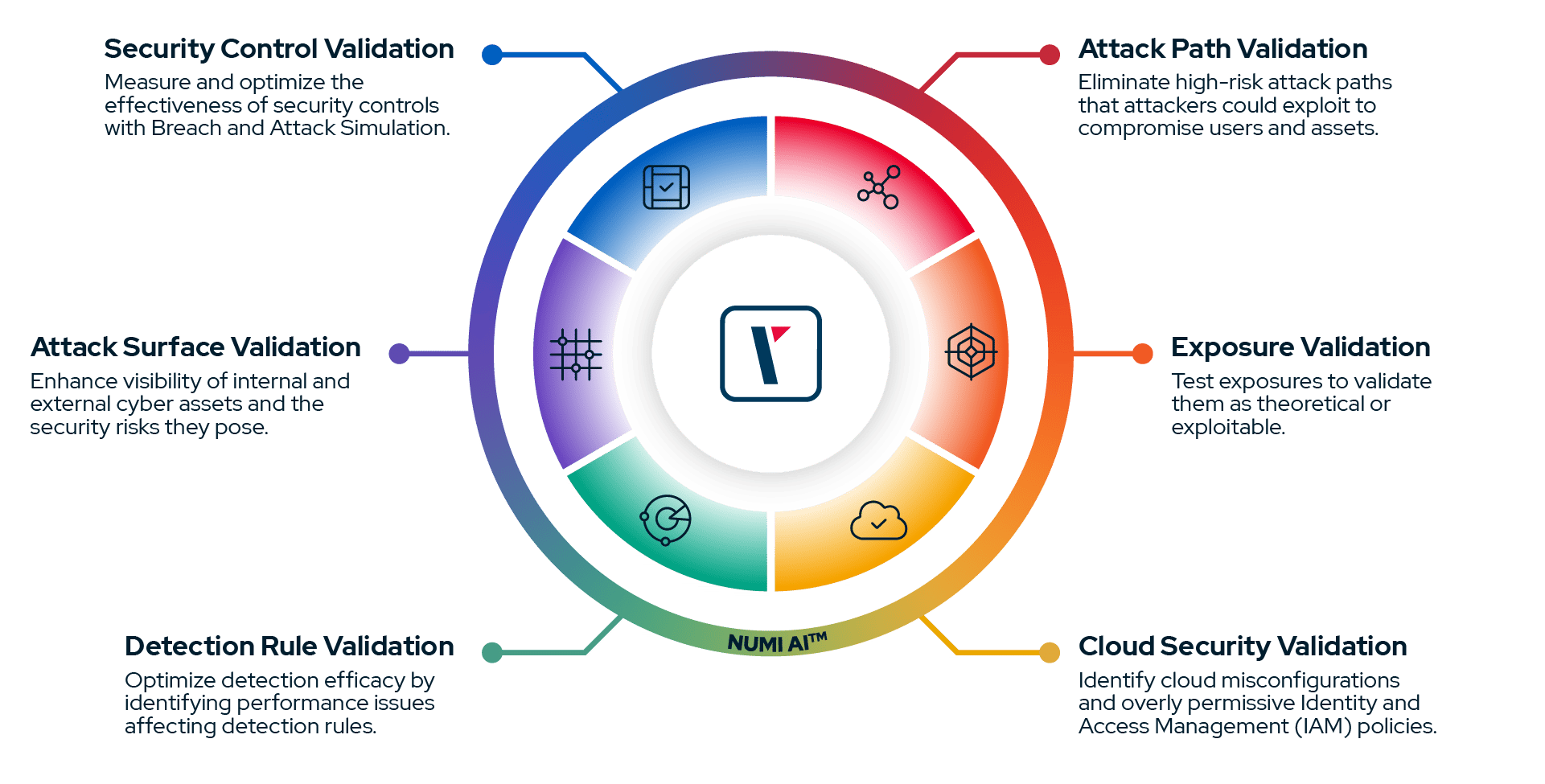
USE CASES
Address Your Unique Security Requirements
Discover how Picus helps you validate, prioritize, and strengthen defenses across every layer of your environment.
Attack
Simulation
Simulate attacks to measure and optimize security controls.
Validation
Improve decision making with a holistic view of your security posture.
Testing
Stay on top of exposures while alleviating manual testing requirements.
OUR VALUE
Block 2x More Threats in Just 90 Days
decrease in high/critical vulnerability backlog.
decrease in Mean Time to Remediate (MTTR) from 74 days to 14 days.
less SLA violations for high/critical vulnerabilities.
less annual labor cost due to reduced prioritization & remediation workload.
Double Your
Threat Blocking
in 90 Days
Continuously correlate, prioritize and validate exposures across siloed data sources. Focus on critical gaps and high-impact fixes to strengthen your security posture.
INTEGRATIONS
Unlock Your Security Stack’s Full Power
Picus integrates with your SIEM, EDR, NGFW, WAF, and the rest of security controls to:
- Safely simulate real-world attacks in production
- Reveal gaps each tool misses
-
Fine-tune each control for maximum efficacy

Visit Our Cybersecurity Glossary
What Our Customer Says
It is no different from a Magician. Ever since we took Picus into our inventory, it has helped significantly to increase our maturity level.
IT Security and Risk Management- Energy and Utilities Industry
Picus completes the task it is required to do perfect as a BAS solution. Threat database is up to date & updated frequently after a new malware or campaign.
IT Security Engineer - Banking
Using Picus, we can conduct risk analysis about possible attacks for their impact on people, processes and technology layers.
IT Manager - Healthcare and Biotech Industry
A very successful platform where we can test the accuracy of our security investments and see their scores.
Manager, IT Security and Risk Management - Manufacturing
Picus is very good attack simulation tool in overall. It shows all security vulnerabilities and guides..
Sr. Information Security & Risk Officer - Banking
There is a very nice team from which I can get quick support. The application provides us with great convenience and confidence in our work.
Information Security Specialist - Transportation
We've been using product for seven years. It's very useful and easily integrated with the network environment and security products.
System Engineer - IT Services
If you have a complex environment and not enough human resource, Picus will help you to prioritize your tasks with its extended detection capabilities.
IT Specialist - Insurance
We have been using Picus more than 1,5 years, we can truly say this product gives us every aspect of our protection. Its suggestions save our times and show us how we are ready for upcoming threats.
CIO - Banking
It helped us a lot in detecting faulty configurations and troubleshooting. It also gave us an idea about the investments we are planning to make.
IT Security and Risk Management - Retail
RESOURCES
Discover Our Latest News and Content









.png?width=3200&height=323&name=Pattern(1).png)
See the
Picus Security Validation Platform
Request a Demo
Submit a request and we'll share answers to your top security validation and exposure management questions.
Get Threat-ready
Simulate real-world cyber threats in minutes and see a holistic view of your security effectiveness.
